Ofisgate Sdn Bhd offers a wide range of Cyber Security services, the most important of which is the Security Posture Assessment (SPA) scope of services. These services offer a comprehensive security evaluation of your network and its associated devices, as well as servers, desktops, web applications, policy, and compliance. Enhance your security posture with our comprehensive Security Posture Assessment services. As a leading cyber security company Malaysia, we leverage our expertise to conduct thorough cyber security audit services, identify vulnerabilities, and provide actionable recommendations for a robust defense against evolving threats. Safeguard your business today.
Our industry experts assist organisations in securing their networks by implementing a thorough Information Security Audit strategy that includes Vulnerability Assessment and Penetration Testing.
Vulnerability Assessment performs scan tests on the client’s network to identify entry points that may be vulnerable to attacks. Penetration testing, on the other hand, infiltrates a computer or a network system in order to reveal any vulnerabilities that an attacker may exploit.
As a trusted Malaysia cyber security company, we leverage cutting-edge technologies and industry best practices to protect your digital assets. From threat detection and incident response to vulnerability management and compliance, our work processes enable us to deliver top-notch cybersecurity services that safeguard your organization against evolving threats. Trust our cybersecurity company Malaysia that provides solutions to protect your business.








Our Security Posture Assessment Services, offered by Ofisgate, a leading cyber security company Malaysia, provide comprehensive evaluations to fortify your organization’s defenses. With a focus on mitigating risks and enhancing resilience, our expert team delivers tailored cyber security services to safeguard your digital assets effectively. Strengthen your security posture and protect your valuable data with Ofisgate’s trusted malaysia cyber security company.
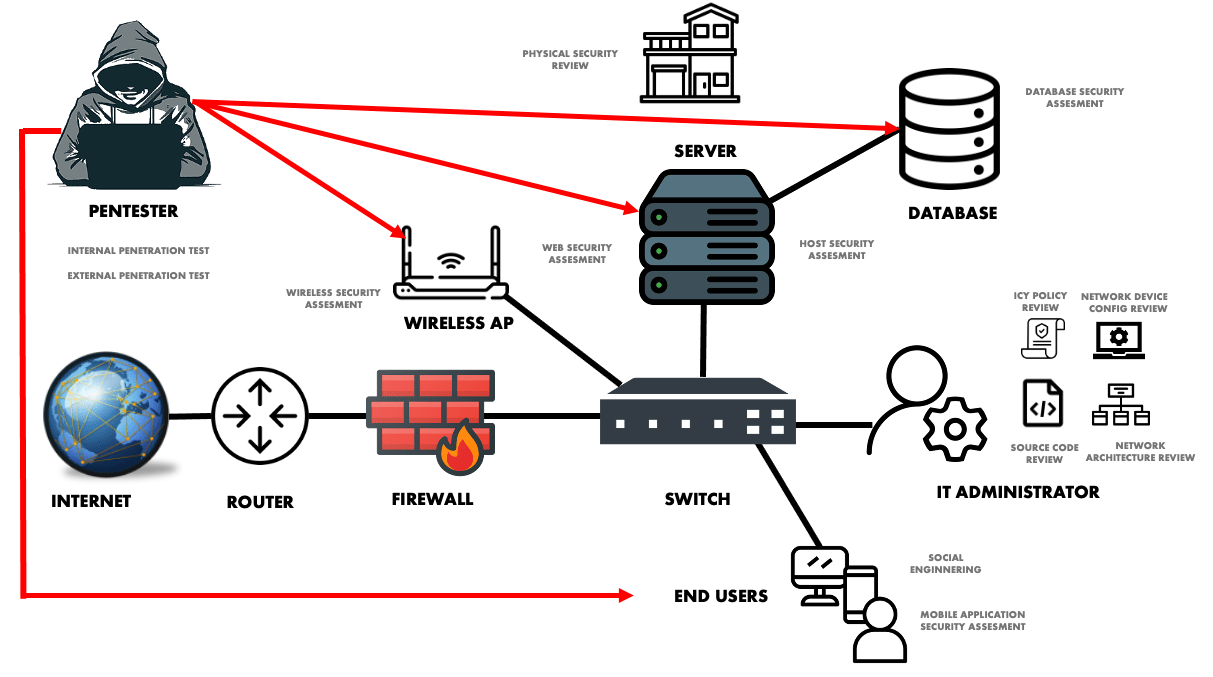
Internal Penetration Tests identify intruder-exploitable vulnerabilities. The basic objective is to identify what an internal network attacker might do. Internal Penetration Testing replicates real-world attackers exploiting internal network vulnerabilities
External Penetration Tests attempts to discover system weaknesses to steal or compromise company data. The test mimics an attacker leveraging external network flaws.
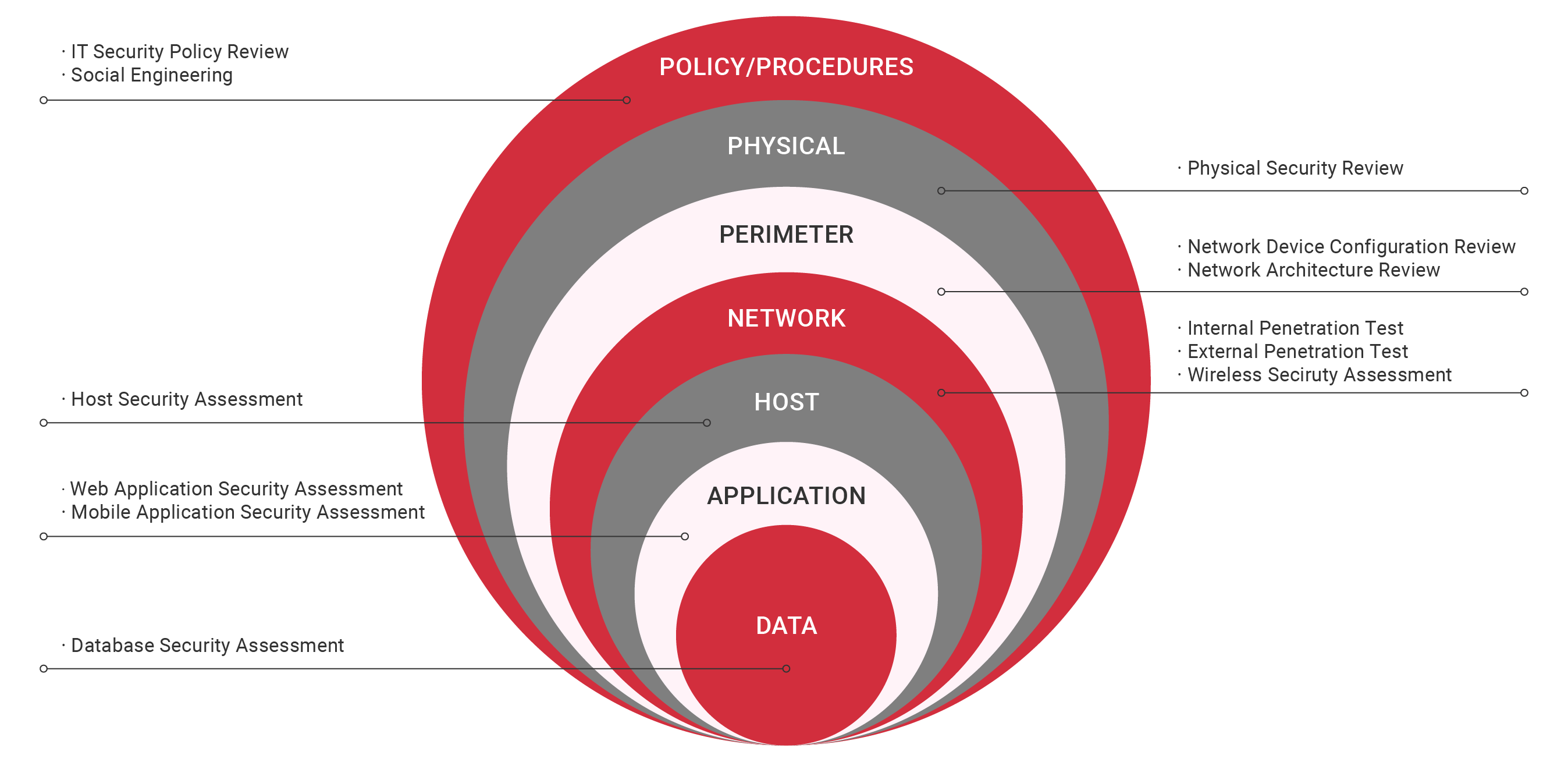
Database security assessment is crucial. It identifies configuration flaws that might compromise it. Specifically, we’ll be able to check whether your database is correctly built, setup, maintained, and consistent with industry standards like CIS Security Benchmark.
Host Vulnerability Assessment is performed the viewpoint of a host console. This ensures that the tested server operating system’s configuration meets the CIS Security Benchmark’s standard operating system security baseline.
Network Design Review identifies weaknesses and proposes improvements to fulfil user network diagram security standards. Our specialists will review the network and security device configurations. We will check that all current policies and regulations are still valid and that any adaptations have been made for the new environment.
Network Device Assessment examines vulnerabilities and configuration. Router, core switch, and firewall configuration files are assessed. This activity finds network device configuration issues and suggests security remedies.
ICT Policy Security Review is carried out with the purpose of evaluating the organisation’s IT operational and procedural security issues. This evaluation is based on industry best practices.
Physical Security Review assess the level of physical security present in the environment of the datacenter and bring to the light any concerns that we have been found toward the customer.
Social Engineering assessing the level of understanding among employees about the implementation of IT security policies.
Mobile Application Security Assessment identifies potential weaknesses in mobile applications (Android and iOS) due to inadvertent misconfiguration, improper platform usage, unintended data leakage, no input validation, insecure data storage, etc.